Two-factor authentication
NAVIGATION Administration > Configuration > Settings > Two Factor Authentication
NAVIGATION Administration > Account > 2FA
PERMISSIONS Administrators manage the two-factor authentication settings for the VSA 10 account. Each user configures their own methods of executing two-factor authentication for their user account.
Two-factor authentication (2FA) is a security process in which a second level of authentication is added to the account login credentials. This feature in VSA 10 has been designed to facilitate security access for users and prevent unauthorized users from accessing VSA account data.
Controlling account 2FA settings
NAVIGATION Administration > Configuration > Settings > Two Factor Authentication
Administrators can control the following 2FA settings for the entire VSA 10 account:
| Setting | Description |
|---|---|
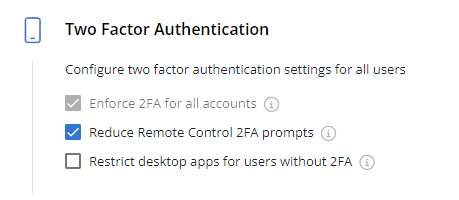
| Enforce 2FA for all accounts |
IMPORTANT Kaseya enforces 2FA for all VSA 10 user accounts. This check box is selected by default upon account provisioning and cannot be changed. Any user in the account who has not yet set up user-level 2FA will be prompted to do so the next time they log in to the VSA 10 web application. |
| Reduce Remote Control 2FA prompts | If this check box is selected, a 2FA prompt will be triggered at login on the Remote Control application but not for each Remote Control session initiated. Refer to Remote Control. |
| Restrict desktop apps for users without 2FA | If this check box is selected, users who have not yet set up user-level 2FA will not be restricted from using the Remote Control application. Refer to Remote Control. |
In the lower-right corner of the page, click Save.
Setting up and executing user-level 2FA
NAVIGATION Administration > Account > 2FA
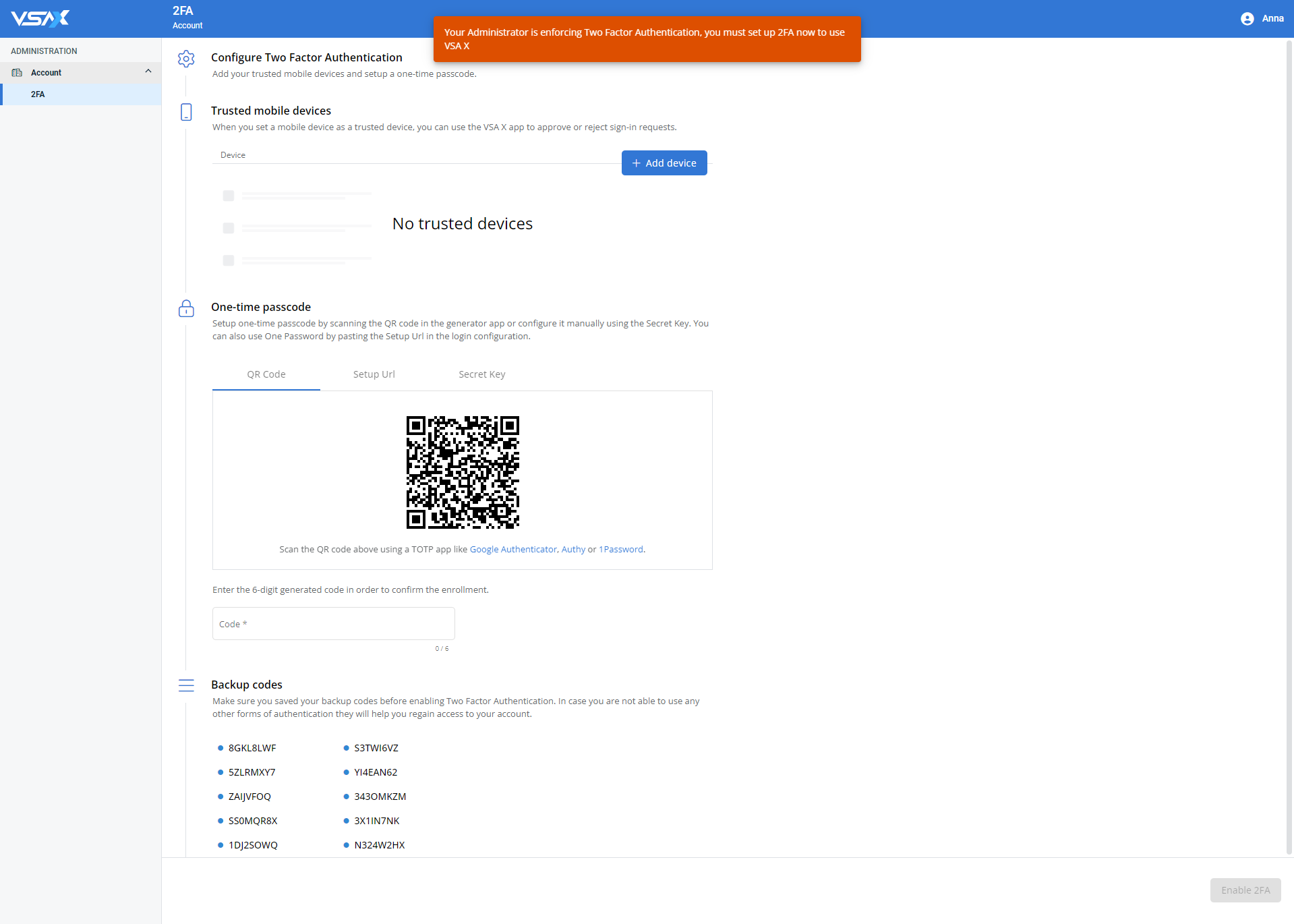
IMPORTANT A user cannot access any area of VSA 10 other than Account > 2FA until they successfully configure their personal 2FA settings. For details, refer to Enforce 2FA for all accounts in Controlling account 2FA settings.
A user must add at least one trusted mobile device or configure one-time passcode generation through an authenticator application. They may also configure both of those options. For details, refer to Trusted mobile devices and One-time passcode.
Users must execute 2FA each time they log in to their user account. For login instructions, refer to Logging in.
The following user-level 2FA options are available after entering your user account password to enter the 2FA page.
| Method | Description | Setup | Execution when logging in |
|---|---|---|---|
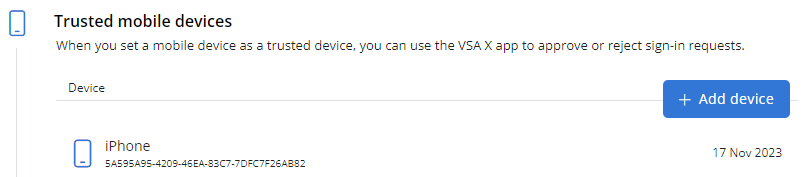
| Trusted mobile devices | Allows you to execute 2FA when logging in to VSA 10 on your current device by automatically receiving a login request on a mobile device (a secondary device) that you have consistent access to. The login request requires manual acceptance. | You must have at least one mobile device registered on your user account to configure this method. Refer to Managing user account device access. In the Trusted mobile devices section, click Add device. Registered mobile devices are available for selection only if the VSA X application is downloaded on them. Click Add devices to add any selected device as a trusted mobile device or click Cancel to close out of the dialog box. NOTE Either this method or the One-time passcode method is required. Refer to Enforce 2FA for all accounts. |
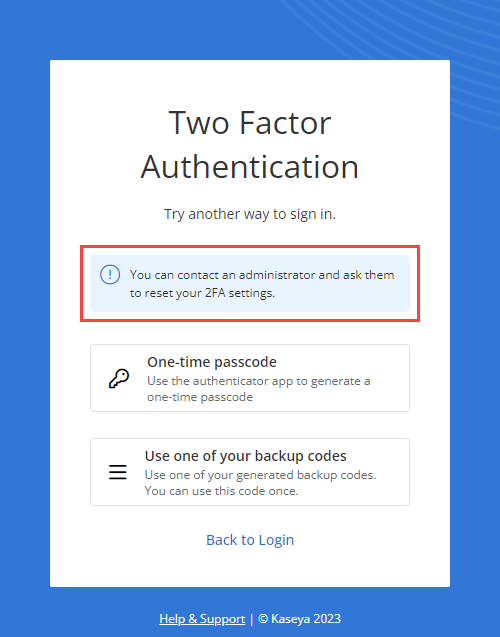
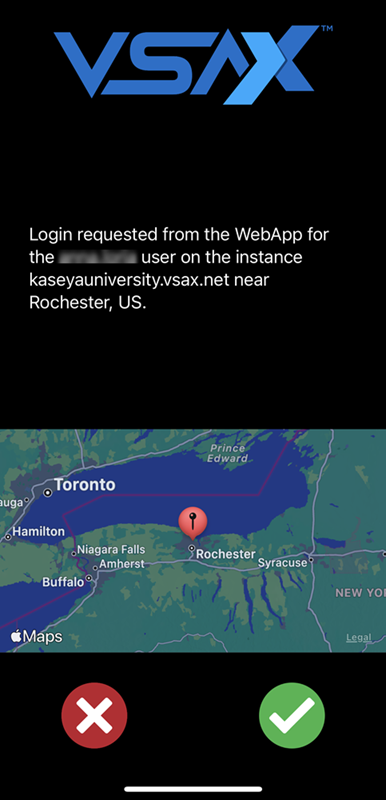
If configured, this method appears as the first option for 2FA during login. A 2FA prompt will be automatically sent to any trusted mobile devices you have added. 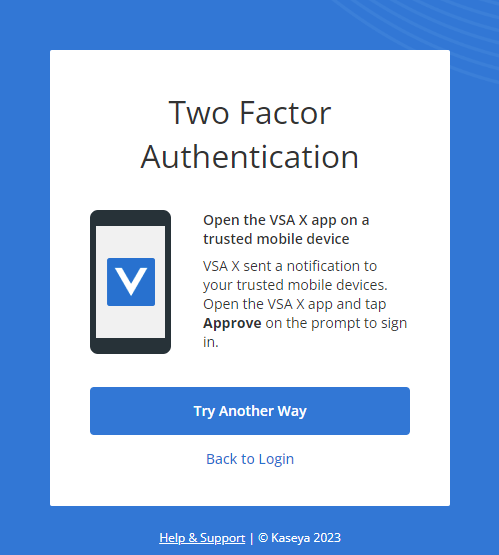 To execute the 2FA, open the VSA X application on your trusted mobile device and click the green check mark in the lower-right corner of the screen. If successful, you will be logged in to your user account. If you wish to bypass this option, click Try Another Way. Depending on whether or not you have the One-time passcode method configured, you will see one of the following alternative options for 2FA. Refer to One-time passcode and Backup codes. |
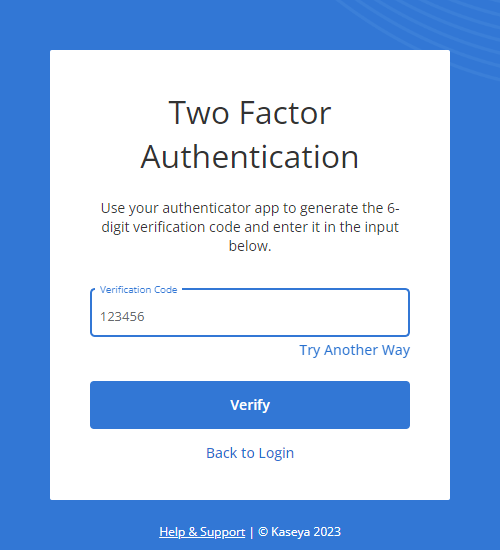
| One-time passcode | Allows you to execute 2FA when logging in to VSA 10 by submitting a time-based one-time password (TOTP). The TOTP is an authorization code generated by an authenticator application that remains valid for a limited time. Examples of authenticator applications include Google Authenticator, Authy, and 1Password. |
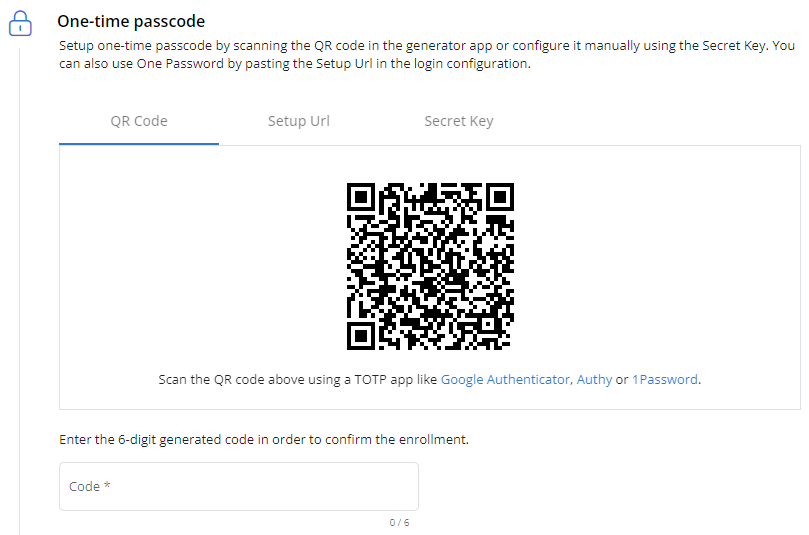
NOTE You should configure an authenticator application, such as Google Authenticator, Authy or 1Password, prior to enrolling in this option. Prospects who are invited to a VSA 10 account via email will be required to configure the one-time passcode method of 2FA upon account creation. Refer to Inviting users to the account. In the One-time passcode section, set up this 2FA method via one of the available tabs:
To confirm the enrollment for any of those methods, enter the six-digit generated code from the authenticator application in the required Code field in VSA 10. NOTE Either this method or the Trusted mobile devices method is required. Refer to Enforce 2FA for all accounts. |
If no Trusted mobile devices are added, this method appears as the first option for 2FA during login. If any Trusted mobile devices are added, this option is available upon clicking Try Another Way. 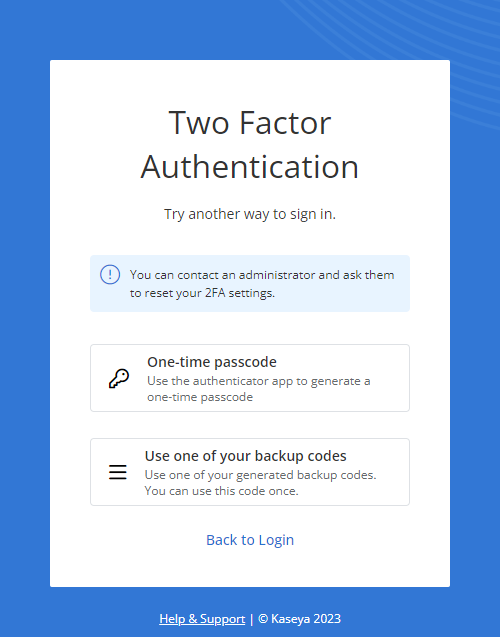 In the Verification Code field, enter the applicable TOTP from your token-generating authenticator application used for 2FA. Click Verify. If you wish to bypass this option, click Try Another Way to use one of your backup codes. Refer to Backup codes. |
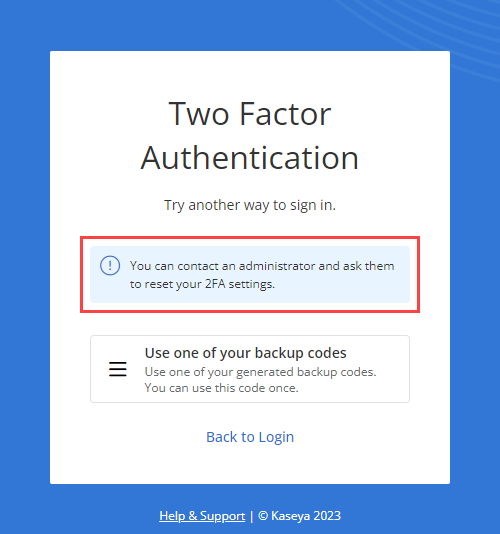
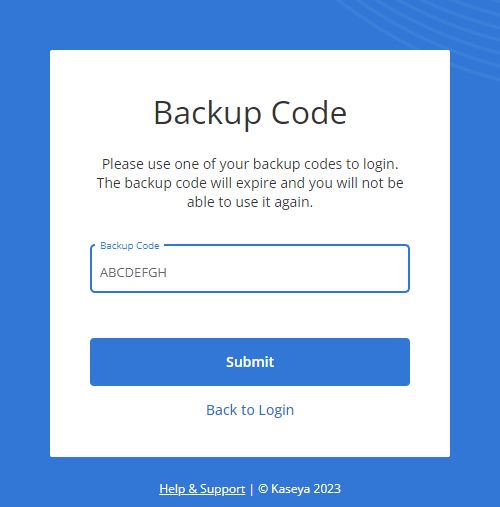
| Backup codes | Each VSA 10 user account is preloaded with 10 unique active backup codes that can be used to execute 2FA in the event that trusted mobile device verification or a one-time passcode via an authenticator app is unavailable. | No setup is required, as the backup codes are preloaded in each user account and remain available as a backup option for 2FA. Used backup codes are automatically crossed out and are not permissible for a second use. If you require a fresh set of backup codes, click Regenerate Codes. Upon doing so, 10 new codes will be generated, and your current codes will no longer be available to use for 2FA. |
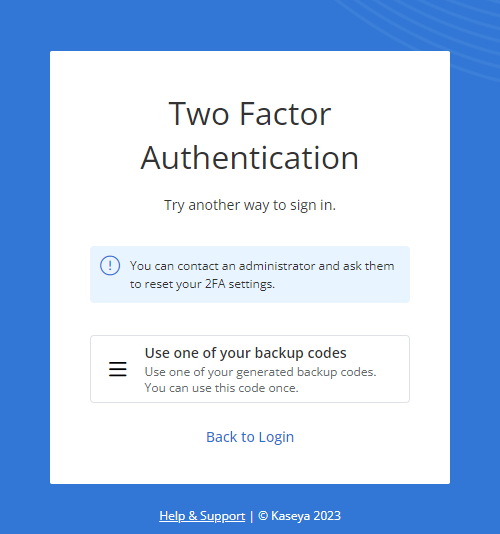
The option to execute 2FA using one of your backup codes becomes available upon clicking Try Another Way from any initial Two Factor Authentication prompt. Click the Use one of your backup codes option, and enter any of the active backup codes for your user account in the Backup Code field. Once you enter a valid eight-digit backup code, click Submit. NOTE Once you use one of your backup codes to log in, we recommend removing it from your saved list of codes, as usage renders a code inactive. NOTE Users are instructed to save their 10 account backup codes in a secure, accessible digital location upon creating their account. If you cannot currently access your backup codes, any administrator in the account can view your active backup codes in your user account details and share them with you. For instructions on how the administrator can do so, refer to 2FA in Viewing and editing user account details. |
NOTE Upon selecting Try Another Way when logging in using 2FA, one of the options presented is to contact an administrator to reset your 2FA. This option refers to the administrator sharing one of your active backup codes. For details, refer to Backup codes in this topic and 2FA in Viewing and editing user account details.