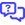Ransomware detection
NAVIGATION Modules > Endpoint Protection > Policies
NAVIGATION Modules > Devices > Device List > select a device
PERMISSIONS Endpoint Protection > View Policy
PERMISSIONS Endpoint Protection > Edit Policy
VSA 10's ransomware detection policy monitors for the existence of crypto-ransomware on endpoints by using proprietary behavioral analysis of files. Once ransomware is detected, VSA can alert you, isolate the device, and attempt to stop the ransomware processes to keep the infection from spreading. When paired with our BCDR solutions, ransomware detection offers a powerful early warning and rapid recovery system against malware.
This topic provides an overview of ransomware detection in VSA 10.
Key benefits
- Know about ransomware infections instantly. Instead of waiting for a user to report the issue, VSA 10 will notify you when files get encrypted by the ransomware. You'll have more time to respond and possibly prevent the spread.
- Easily monitor by using policy-driven configuration. The policy-driven approach of VSA 10 enables MSPs to monitor targeted devices easily and at scale for the presence of ransomware. Integrations with key MSP tools, such as Autotask, BMS, and ConnectWise, along with email notification options, ensure that the right resources can be immediately alerted if ransomware is detected.
- Prevent spreading of ransomware with automatic network isolation. Once ransomware is detected, VSA 10 can isolate the affected device from the network and attempt to stop suspected ransomware processes to prevent further spread of the infection to other devices.
- Remediate issues remotely. Devices automatically isolated from the network can still contact VSA 10, enabling you to take effective action to resolve the issue.
- Recover with Datto Continuity products. When VSA 10 is integrated with a Professional Services Automation (PSA) platform and Datto BCDR, you can quickly recover from the ransomware outbreak by restoring the device to a previous state.
Requirements
- You must have an active VSA subscription.
- Your Ransomware Detection license must be active. You can check its status by navigating to Endpoint Protection > License in your VSA 10 instance.
- Ransomware detection must be enabled and configured. For more information, refer to Create a ransomware detection policy.
- The VSA 10 Agent must be installed on all endpoints you wish to monitor, and those devices must be able to communicate with your VSA 10 instance.
Supported operating systems
The ransomware monitor is supported by Windows 8.1 and up only.
Ransomware monitor features
You can configure ransomware monitoring to scan an entire host or only the paths you specify. You can also designate the action it takes when it suspects an infection on a host. The ransomware monitoring policy includes the following features:
- Scan parameters that enable you to choose between scanning all local drives on an endpoint or only specific drives. For further granularity, you can designate specific paths on the host to monitor.
- Host isolation that automatically terminates all of the endpoint's network connections except to the VSA portal, which helps prevent the spread of ransomware to other endpoints. You can augment host isolation with custom policies that attempt to terminate known ransomware processes when they are detected, slowing or stopping the spread of ransomware on the infected host.
How to...
Ransomware detection is enabled and enforced via policies. To start protecting your customers against ransomware, you'll first need to define a policy that identifies which devices VSA 10 should monitor and what actions it should take when it identifies a potentially compromised device. Perform the following steps to create and activate your policy:
-
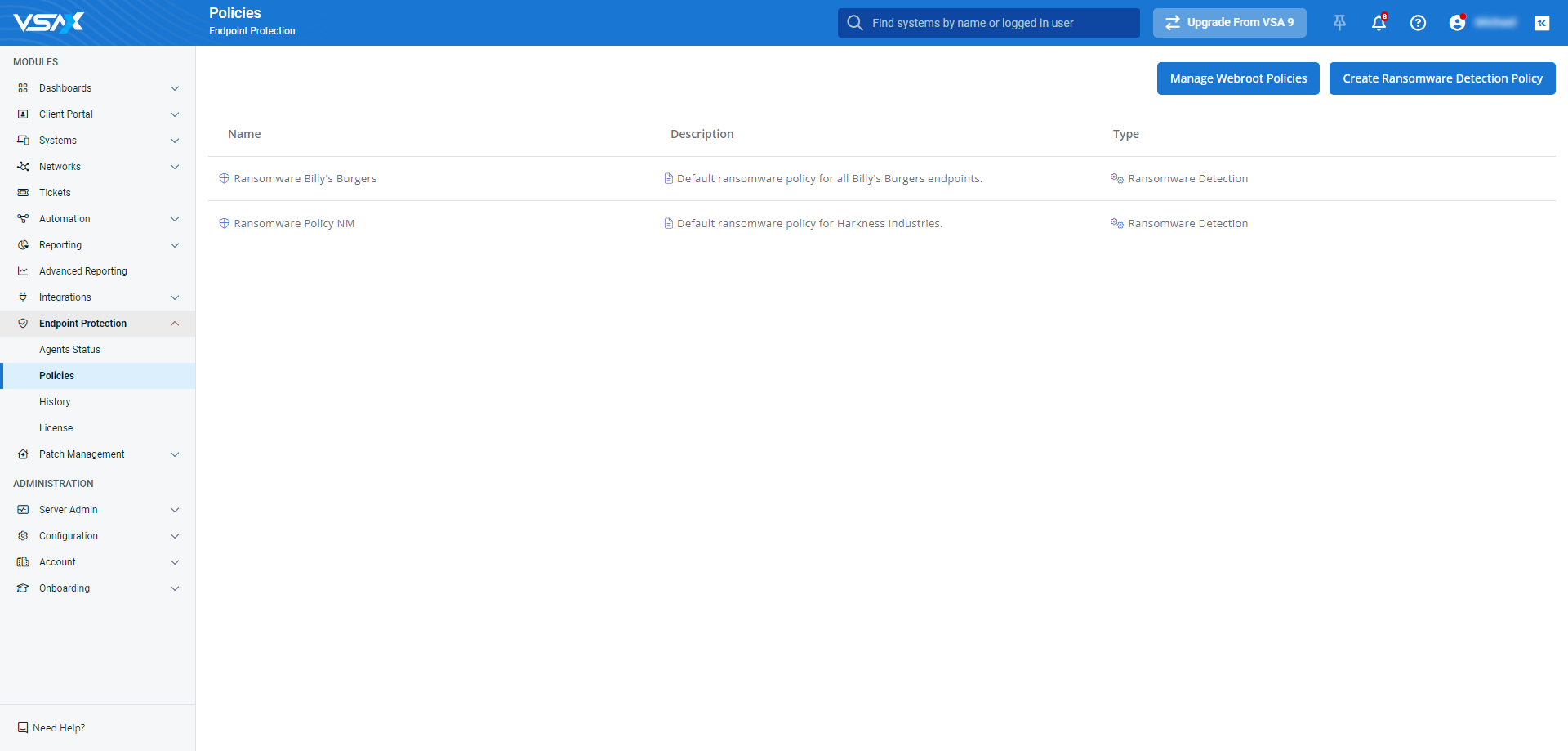
From the left navigation menu in VSA 10, navigate to Endpoint Protection > Policies.
-
On the Policies page, click Create Ransomware Detection Policy.
-
The Create Policy page will load.
-
Configure the following settings:
Setting name Definition Name
Name of the policy
Description Brief description of the policy's purpose
Notification Priority Alert level that VSA will use if it detects suspected ransomware
Detection Scope All Local Drives By default, Ransomware Detection tracks changes to your operating system volume only. Click the All Local Drives check box to expand change tracking to all internally-mounted disks on the endpoint. Network drives, removable drives, and USB mass storage devices are excluded from being monitored. Add If there are additional paths on the host you'd like ransomware detection to analyze, click Add and enter a path to be monitored; we do not recommend adding network drives, removable drives, or USB mass storage devices. Excluded Folders Excludes specific folders and file types from scanning
Excluded File Extensions Automatically kill malicious processes Attempts to terminate suspected malicious processes when they are detected, reducing the impact of a ransomware attack
Automatically isolate infected systems Isolates the endpoint from all network connections except for VSA 10 when suspicious processes are detected; if successful, Automatically shutdown infected systems will not execute
Automatically shut down infected systems
Attempt to shut down infected devices if suspected ransomware is found; if Automatically kill malicious processes or Automatically isolate infected systems are also enabled, VSA will attempt to complete those steps first; if Isolate host is successful, the shut down response will not execute
-
Click Save. Then, proceed to the next section of this article.
Once you've created the ransomware policy, you'll need to assign it to the devices you'd like to monitor. Perform the following steps to do so:
-
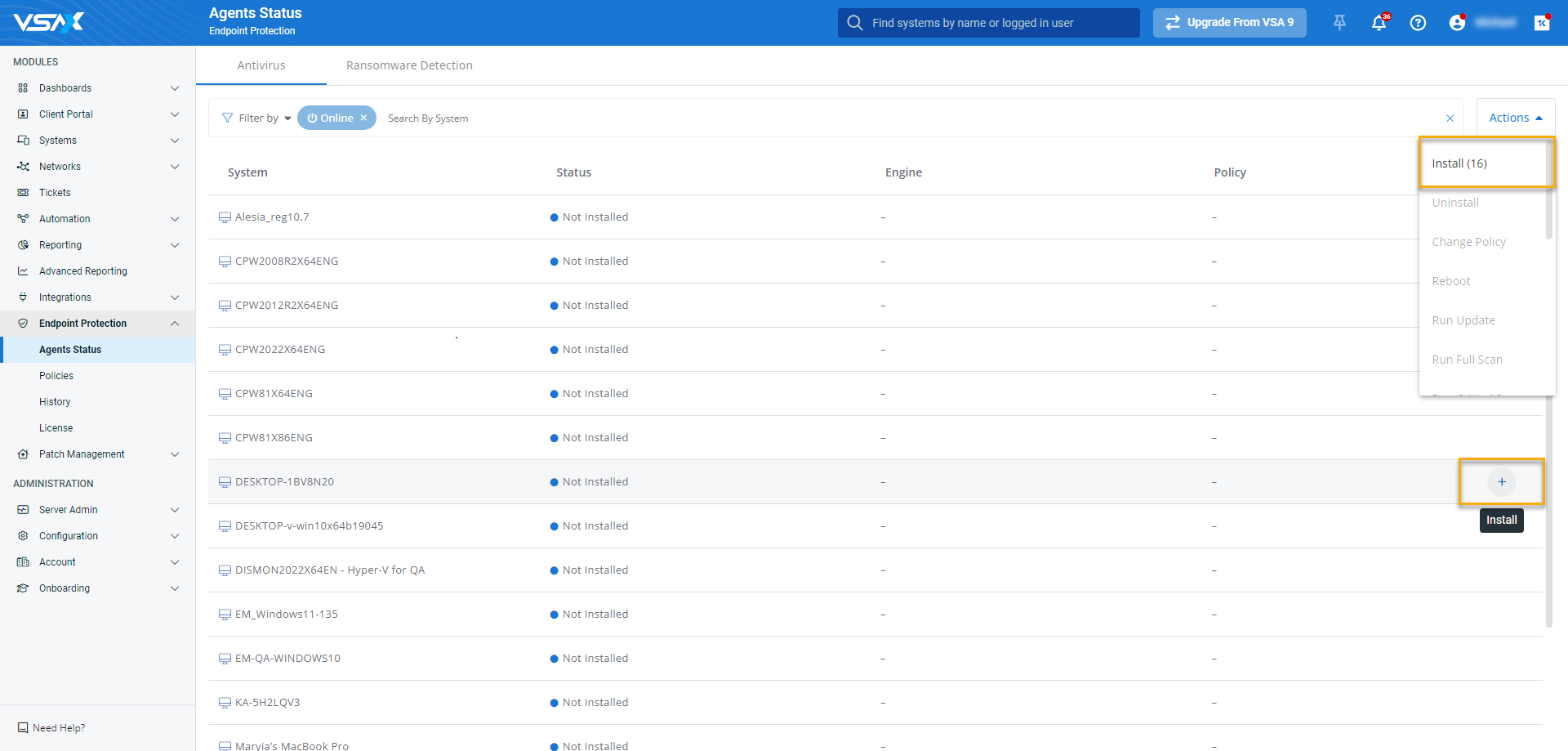
From the left navigation menu in VSA 10, navigate to Endpoint Protection > Agents Status.
-
Select Ransomware Detection from the top navigation bar.
-
Use the Search by System field to filter the page to the device or devices you'd like to manage.
-
Click Actions > Install to apply the policy to all eligible devices in the current view. To apply the policy to an individual device, move your mouse over its list entry and click the
 icon that appears.
icon that appears. -
The Install Policy modal will open. Select the policy you'd like to apply.
-
Click Apply Policy Update. Ransomware detection will enable for all of the devices you selected. To check the status of the ransomware policy on an individual device, proceed to the next section of this article.
To check the ransomware detection status for an individual device, perform the following steps:
-
In your VSA instance, navigate to Devices > Device Management or Devices > Device List.
-
Locate the device you'd like to review and click its entry in the list. For more information about searching for devices, refer to Finding and managing devices and Viewing device details.
-
In the system details pane, scroll to the Software section.
-
The Monitoring Status field indicates whether the endpoint is currently protected by a ransomware detection policy. The Threat Detected field surfaces whether VSA 10 suspects ransomware is present on the device. The Network Isolated field details whether the device is currently isolated from the network in response to any suspected threat.
If you receive a ransomware notification about a protected device, you can evaluate the threat and take action by performing the following steps.
-
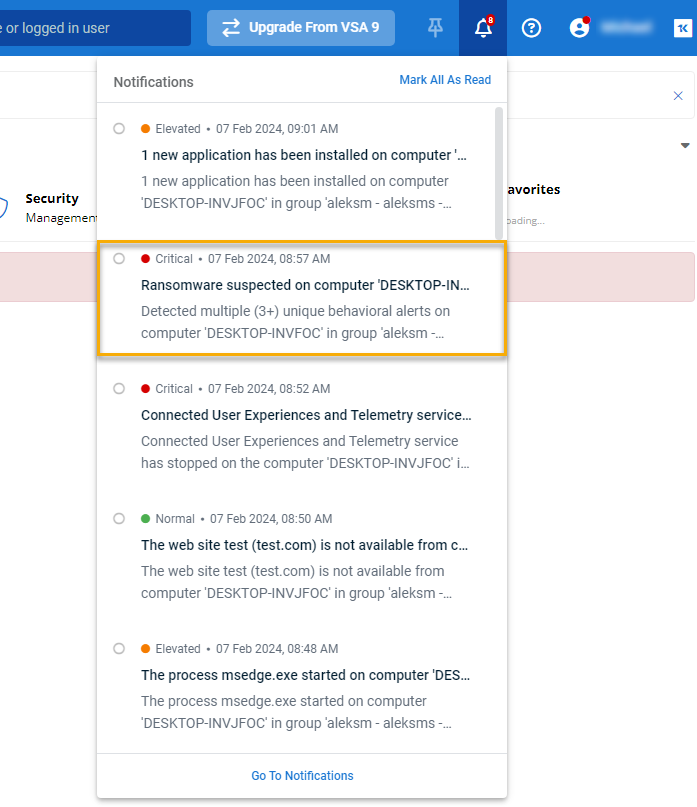
In the VSA 10 top navigation bar, click the
 icon.
icon. -
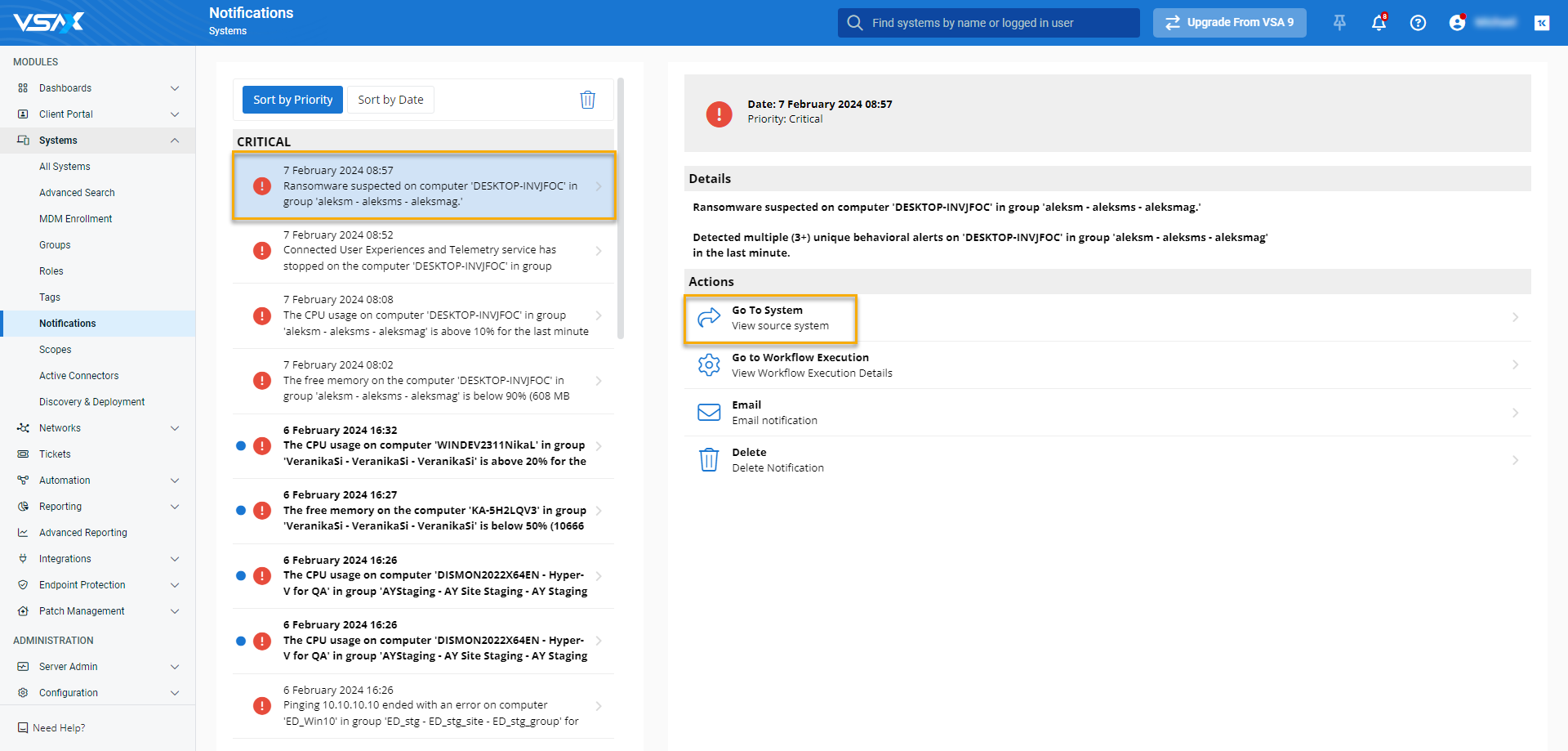
The ransomware alert will appear in the application's feed. Click Go To Notifications.
-
On the alert detail page , you can review extended information about the notification. To take action, click Go To System.
-
In the system details pane, scroll to the Software section.
-
Click the Security option.
- The Security pane will load. Scroll to the Ransomware Detection section.
-
If the computer has not already been isolated from the network by your ransomware policy, click Network Isolated. Isolating the computer interrupts all network connections except for those required to reach the VSA 10 servers. Doing so can help stop the spread of ransomware to additional endpoints.
-
Once the computer is isolated, you can use VSA 10's management features to triage and remediate the incident. To learn more about available device management options, refer to Controlling devices.
Ransomware detection FAQ
The following frequently-asked questions will help you get the most out of your ransomware detection license.
Setting up ransomware detection is as easy as enabling it from the Endpoint Protection > Policies page in VSA 10. To get started, refer to Create a ransomware detection policy.
Ransomware detection is designed to work alongside other security products you deploy to your customer endpoints.
Device isolation can be reverted by clicking Network Isolated > Revert Isolation in the device details pane. Doing so will revert any isolation that has occurred on a device, reboot the device, and return its ability to contact the internet and other devices on the network. Refer to Respond to a ransomware alert.
Enter the full directory path, one per line. For example:
- C:\Users\admin\F1
- C:\Users\admin\F2
The VSA 10 ransomware detection engine looks for the existence of crypto-ransomware on endpoints by using proprietary behavioral analysis of files.
You can run a simulation package to test VSA 10's ransomware detection. The simulation package (AutoRS.zip) and a set of instructions (Readme.txt) are available to download here.
NOTE How to get or run real ransomware is outside the scope of this procedure. The change described here is intended for demonstration purposes only and should never be left in place on an endpoint after the demonstration is complete.
VSA detects ransomware attacks by analyzing file update behavior and detecting file encryption. To test detection of ransomware, follow these steps:
- Configure VSA with ransomware detection enabled. Refer refer to Create a ransomware detection policy.
- Create a folder under the root (for example, C:\User\).
- Place a number of normal-sized user files in the folder (30 to 50 files or more). There should be several different types of files; for example, graphic files, text files, and so forth.
- Wait at least three minutes before starting the ransomware to avoid files being considered as transient.
- Download and start the ransomware. It can take up to a minute or more before the encryption process starts, depending on the type of ransomware.
- If the ransomware begins to encrypt files, VSA should create an alert and try to isolate the host.
IMPORTANT Do not create the folder in the Program Data, AppData, Temp directories or in any other folder not normally targeted by ransomware.
If VSA does not create an alert, check the following:
- If the files in the user folder were not renamed or deleted, it is a sign that the ransomware did not start up or perform any encryption. This behavior can happen for many reasons; for example, the ransomware is outdated, the remote website the ransomware software attempts to connect to is no longer active, it has detected that it is running in a virtual machine, or it has detected that the keyboard of the machine is Russian or Ukrainian.
- If antivirus software is installed, it could block the ransomware. You should disable antivirus software and similar programs when testing.
- Simulation software, such as Ransim from KnowBe4, cannot be used directly because VSA detects that it is originating from a safe application. Use the modified version available from Datto instead. Refer to Can I test ransomware detection?
- If none of the above explained the missing alert, please contact Kaseya Support.
We tested VSA 10's ransomware detection with Datto RMM. Testing included the following:
- Testing the effectiveness of ransomware detection against current strains of ransomware in the wild
- False positive tests where ransomware detection was used alongside legitimate apps that mimic malicious ransomware behaviors
- Performance testing to check impact on system performance for devices running ransomware detection
In addition, we continuously update ransomware detection's threat definitions as new strains are identified.
We store the ransomware detection log on protected endpoints at <VSA X installation folder>\RWD\engine.log.
You can also view details about ransomware alerts from your VSA portal. For more information, refer to Audit Log.
Need support?
Kaseya is always available to assist further. Your Kaseya Account Executive can enroll you in basic and intermediate-level platform training. For technical assistance, visit our Kaseya Helpdesk article to learn how to get in touch.