Workflow Templates
NAVIGATION Modules > Automation > Workflows
PERMISSIONS Automation > View Tasks & Scripts
PERMISSIONS Automation > Run Tasks & Scripts
PERMISSIONS Automation > Edit Tasks & Scripts
The in-product Workflow templates library delivers immediate value by enabling the automation of essential tasks that improve system security, operational efficiency, and compliance across an organization’s device fleet. These templates address a variety of needs—from troubleshooting, automatic remediation, application deployment to auditing system settings, enforcing security policies, and monitoring system health. By standardizing these processes, workflows minimize human error and ensure consistency across all devices.
This article describes how Workflow templates can be used, and what Workflow templates are available.
For security and compliance, templates such as Audit BitLocker Status, Disable SMBv1 Protocol, and Disable USB Mass Storage Support proactively identify and remediate vulnerabilities, helping organizations meet security standards. These automated checks and configurations strengthen the organization’s defense against potential threats by ensuring that devices are configured with the latest security best practices.
On the operational side, templates like Device On-boarding, Run System Disk Cleanup, Deploy Custom Fonts, Deploy MSI and EXE Files and Clear Windows Update Services Cache automate routine and repetitive maintenance tasks that enhance device performance and extend system longevity. These automations help prevent unnecessary downtime and ensure that devices operate smoothly with minimal intervention.
Additionally, templates that facilitate user interaction, such as Ask For User Approval To Reboot Device and Send Message If Uptime Is More Than 10 Days, improve communication between IT and end-users. This functionality minimizes disruptions by allowing users to manage reboot timing and receive timely reminders, supporting a smoother IT experience.
Overall, these Workflow templates simplify complex tasks, increase productivity, and enable IT teams to focus on strategic initiatives by automating routine but essential processes. Through this automation, organizations benefit from improved security, better compliance, and enhanced device performance.
Accessing the Workflow Template Library
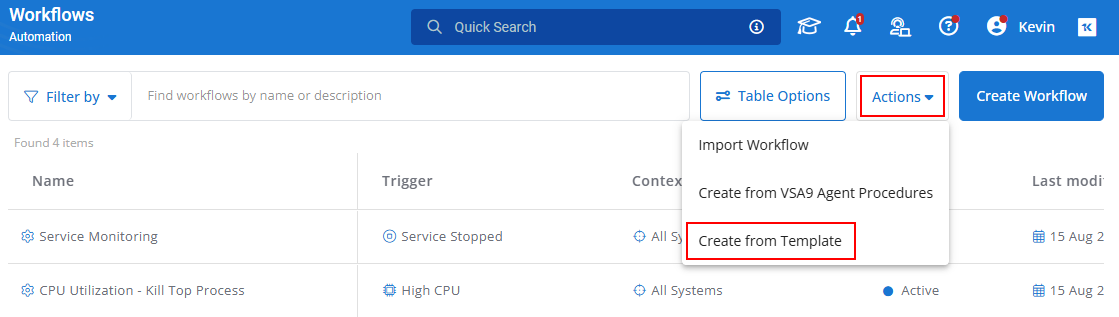
The Workflow Template library can be accessed by navigating to a location within the User Defined folder, and clicking Create from Template. This will open the Create from Template window.
From there, you can sort the list of Workflow templates by any of the available columns.
Click on any of the available templates to view and edit it before creating a workflow based on that template. For more information on creating and editing workflows, refer to Workflows.
Available Workflow Templates
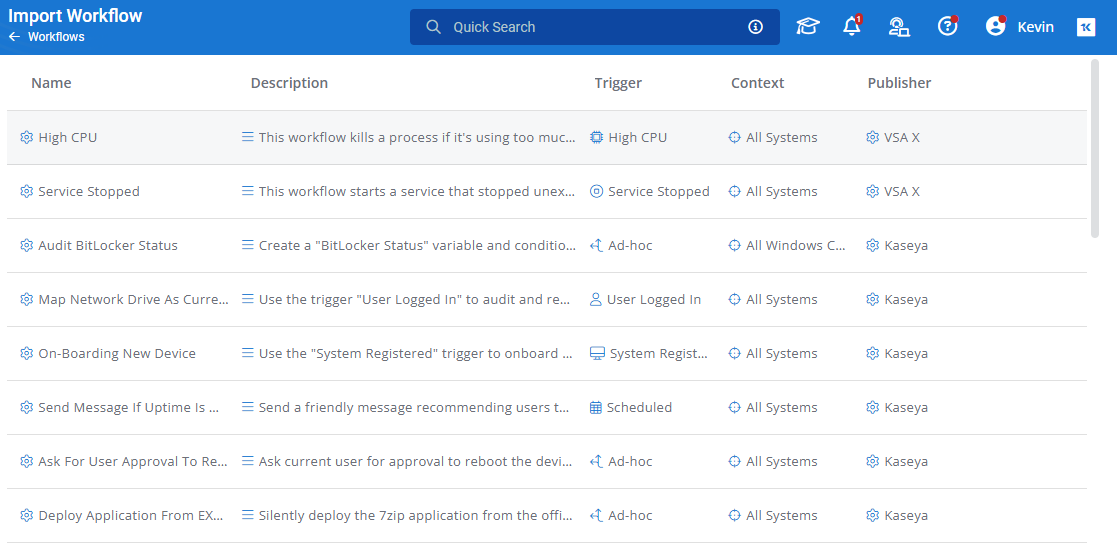
The following is a list of the currently available Workflow templates and their usage. For full details on each Workflow, view them in the Workflow template library in VSA 10.
- Ask For User Approval To Reboot Device
- Prompts users to approve a system reboot, ensuring they are notified before the restart occurs. Checks if user input permits the reboot to proceed, which minimizes disruption to ongoing tasks.
-
Audit And Remediate Missing Network Printer
- Detects the presence of a network printer on a device and, if missing, automatically installs it. Helps ensure critical printers are consistently available across networked devices.
- Audit BitLocker Status
- Checks the BitLocker encryption status on Windows devices, verifying whether drives are protected by encryption to support data security compliance.
- Audit Certificates Expiring Within 30 Days
- Reports in the Workflow Action Log and sends an email if any certificates are expiring within 30 days.
- Audit Installed Apps For Current User
- Gathers and reports applications installed for the current user, assisting with software inventory management and detecting unapproved software.
- Audit Windows Firewall Status
- Reviews the Windows Firewall status, confirming if it is enabled or disabled. Useful for security audits to ensure firewalls are consistently active across devices.
- Clean Up Printer Queue
- Stops the Print Spooler service, clears the printer queue, and restarts the service on Windows computers.
- Clear Windows Update Services Cache
- Clears the cache of the Windows Update service, addressing potential update-related issues and ensuring efficient update processing.
- Create System Restore Point
- Verifies if a System Restore Point has been created within the past 10 days and if absent, creates one.
- Deploy Application From EXE File
- Installs a custom application from an EXE file.
- Deploy Application From MSI File
- Installs a custom application from MSI package.
- Deploy Custom Font
- Downloads and install a custom font in the Fonts folder to ensure that devices have access to specific fonts for standardization or branding.
- Deploy Datto EDR/AV
- Installs the Datto Endpoint Detection and Response (EDR) or Antivirus solution on target devices to enhance endpoint security and standardize antivirus protection across an organization.
- Deploy Datto Endpoint Backup
- Installs Datto Endpoint Backup on target devices, automating the setup for backup services, which is crucial for data recovery and business continuity.
- Deploy RapidFire Tools Discovery Agent
- Installs the RapidFire Tools Discovery Agents on Windows devices.
- Deploy RocketCyber Agent
- Installs the RocketCyber Agent for threat detection and monitoring, enabling centralized management of endpoint security services.
- Detect Unapproved Apps
- Audits devices for unapproved applications getting installed, and if MSI based, attempts to uninstall.
- Disable FastBoot on Windows Computers
- Disables the FastBoot feature to ensure full shutdowns instead of partial hibernations. Useful for systems that require consistent startup conditions.
- Disable SMBv1 Protocol On Windows Computers
- Audits and disables the SMBv1 protocol to reduce vulnerabilities associated with the outdated protocol, improving security by enforcing modern network protocols.
- Disable USB Mass Storage Support
- Disables support for USB mass storage devices to prevent unauthorized data transfer via USB devices.
- High CPU
- Kills the top process on a device if a high CPU notification is triggered.
- Map Network Drive As Current User
- Maps a specified network drive for the current user, automating access to shared resources and simplifying resource accessibility across networked devices.
- Office 365 Quick Repair
- Initiates a quick repair of the Office 365 installation to address common issues without a full reinstallation, which is useful for troubleshooting Office-related problems.
- On-Boarding New Device
- Uses the System Registered trigger to on-board new devices. This workflow runs any assigned patch policy on Windows computers and servers right after they are added.
- Run Assigned Patch Policy on Windows Computers
- Allows you to manually runs the patch policy assigned to a Windows device. This will include OS patches and any 3rd part apps part of the policy.
- Run System Disk Cleanup On C Drive
- Runs the Disk Cleanup utility on the C drive to free up space by removing unnecessary files, improving system performance through optimized storage.
- Run Windows Defender Quick Scan
- Initiates a quick scan using Windows Defender, providing basic malware protection checks essential for regular system health verification.
- Send Message If Uptime Is More Than 10 Days
- Checks device uptime, and if it exceeds 10 days, sends a notification message to help enforce reboot policies for maintaining system performance and security.
- Service Stopped
- Automatically restarts a service that has stopped unexpectedly.
- Set Balanced Power Plan
- Configured the power settings to use a balanced power plan on Windows Computers.
- Set Desktop Wallpaper for Current User
- Sets a custom desktop wallpaper for the current user, allowing for personalization or branding of desktop environments.
- System Offline
- Checks if a device is offline and sends notifications as needed, which is helpful for ensuring that critical systems remain online and responsive.
- Unapproved Application Added
- Detects and reports unapproved applications added to devices, supporting compliance and security protocols by monitoring new software.
- Use Webhook To Send Teams Messages
- MS Adaptive Cards teamplates to be used as notifications to Microsoft Teams via a webhook, automating alerts and improving communication for team collaboration.